Useful commands

Today it occurred to me that there are commands and code snippets that I keep having to hunt down that I should start documenting for myself but also for others who might benefit from having them. Below is what I hope to be the beginning of an ongoing series of scenarios and the commands that helped address the scenario.
Command #1
Today we needed to get the specific version number of a number system files. Normally to check a specific file version you open up Windows Explorer, navigate to the file, right-click then choose properties then navigate to the Details tab then read off the File version information.
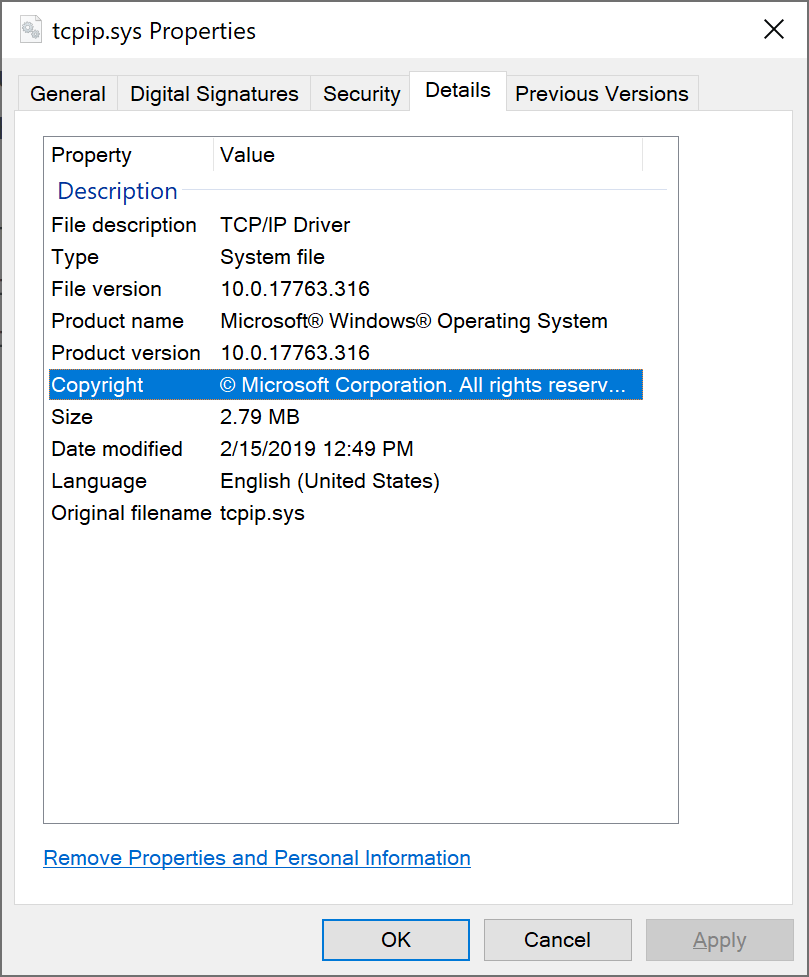
This works great if you are just checking one or two files on a single system but if you need to check the same files across many systems this becomes a real chore. PowerShell to the rescue! The same process can be accomplished via PowerShell as follows:
(Get-Item $env:windir\system32\drivers\tcpip.sys).VersionInfo | Select FileVersion,FilePrivatePart
This generates a much cleaner output as follow:
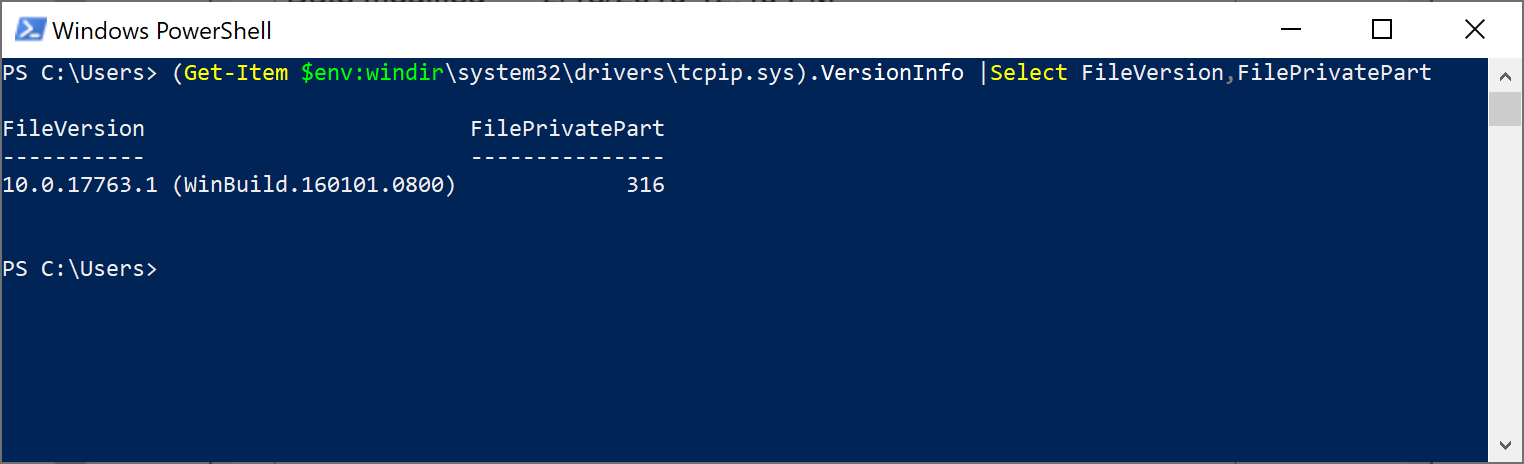
The above command when wrapped in additional scripting could very easily be run across multiple systems at once reporting back the file versions without the need to manually log into each system to go through the manual process.
Command #2
In my job we often need to look at simultaneous packet captures from both ends of a network conversation. While there are many tools out there to perform network captures I often get asked "Can't we just do this with netsh and filter capture to just the IPs we are interested in?" Well after a bit of research the answer turns out to be yes! The full list of filter parameters for netsh is available here. What the end command ends up looking like is something like this:
netsh trace start capture=yes tracefile=c:\temp\capture.etl maxsize=2048 filemode=circular overwrite=yes report=no correlation=no IPv4.SourceAddress=(192.168.0.1,192.168.0.2) IPv4.DestinationAddress=(192.168.0.1,192.168.0.2) Ethernet.Type=IPv4
As normal once the issue has been reproduced the capture is stopped by running:
netsh trace stop
What you will end up with though is a .etl of the packet capture which contains just the traffic between 192.168.0.1 <-> 192.168.0.2. Microsoft Message Analyzer can be used to import the capture and read the results or export to .cap format that can then be viewed in WireShark.